(Updated: February 27, 2025; 9:40 am) This blog was updated to reflect the latest updates on the Hack of Bybit.
On February 21, 2025, Bybit, an eminent exchange of cryptocurrency, experienced a significant security violation resulting in the loss of nearly $ 1.5 billion in ether (ETH). This incident is the biggest digital robbery in the history of cryptocurrency. Fortunately, Bybit actively collaborates with industry experts, including the analysis channel, to retrace stolen assets. They also launched a recovery premium program, offer up to 10% From the amount recovered from people who help recover the stolen crypto.
In this blog, we will examine how the feat happened; Tactics, techniques and procedures of attackers (TTPS) and their consistency with the Democratic People’s Republic of Korea (RPDC); And how the chainysis collaborates with the police and the police to help recover the funds.
Details of Bybt’s feat
Bybit’s hacking serves as a sudden recall of the evolutionary tactics used by cybercriminals sponsored by the State, in particular those linked to RPDC. As we recently revealed in our Crypto Crime 2025 report, pirates affiliated to North Korea stole approximately $ 660.5 million out of 2023 in 2023. In 2024, this number increased to $ 1.34 billion stolen out of 47 incidents – an increase of 102.88% of the stolen value. Bybit’s hacking alone has led to nearly $ 160 million more stolen than all funds stolen by North Korea throughout 2024.
This attack highlights a common gaming book used by the RPDC: orchestrating social engineering attacks and using complex whitening methods to try to move non -detected stolen funds. Bybit’s feat funds have also consolidated in addresses with funds from other known attacks linked to PDR, providing additional evidence that the actors of the national state are behind this last incident.
You will find below a step by step analysis of how the exploitation of the reverse took place:
- The compromise: The hackers had a safe developer access to the computer to control the safe user interface that was specifically used for Bybit transactions. They then added the malicious javascript cut in the frontal code, to reveal that Bybit signed a legitimate transaction, when in fact it was malicious.
- Initiation of unauthorized transfers: During what seemed to be a routine transfer from the Cold Portfolio Ethereum de Bybit to a hot wallet, Bybit signed the malicious transaction without knowing, allowing attackers to move around 401,000 ETH – evaluated at nearly $ 1.5 billion at the time of the feat – addresses under their control.
- Dispersion of active ingredients through intermediate portfolios: The stolen assets were then moved through a complex network of intermediate addresses. This dispersion is a current tactic used to obscure the efforts to follow trails and hinder blockchain analysts.
- Conversion and whitening: The pirates exchanged important parts of the stolen ethn for tokens, including BTC and DAI. They also used decentralized exchanges (DEX), transverse bridges and an instant exchange service without KYC to move assets through the networks.
- Keep dormant funds and strategic money laundering: A notable part of the stolen funds has remained inactive in various addresses, a deliberate decision often used by pirates affiliated to North Korea. By delaying laundering efforts, they aim to survive an in -depth examination which generally immediately follows high -level violations.
Below Chain reactor Until now, the graph presents the complexity of laundering efforts: the network of intermediate addresses, exchanges of tokens and transversal movements which try not only to obscure the stolen funds, but also demonstrate the large -scale consequences of this feat through the broader cryptographic ecosystem.
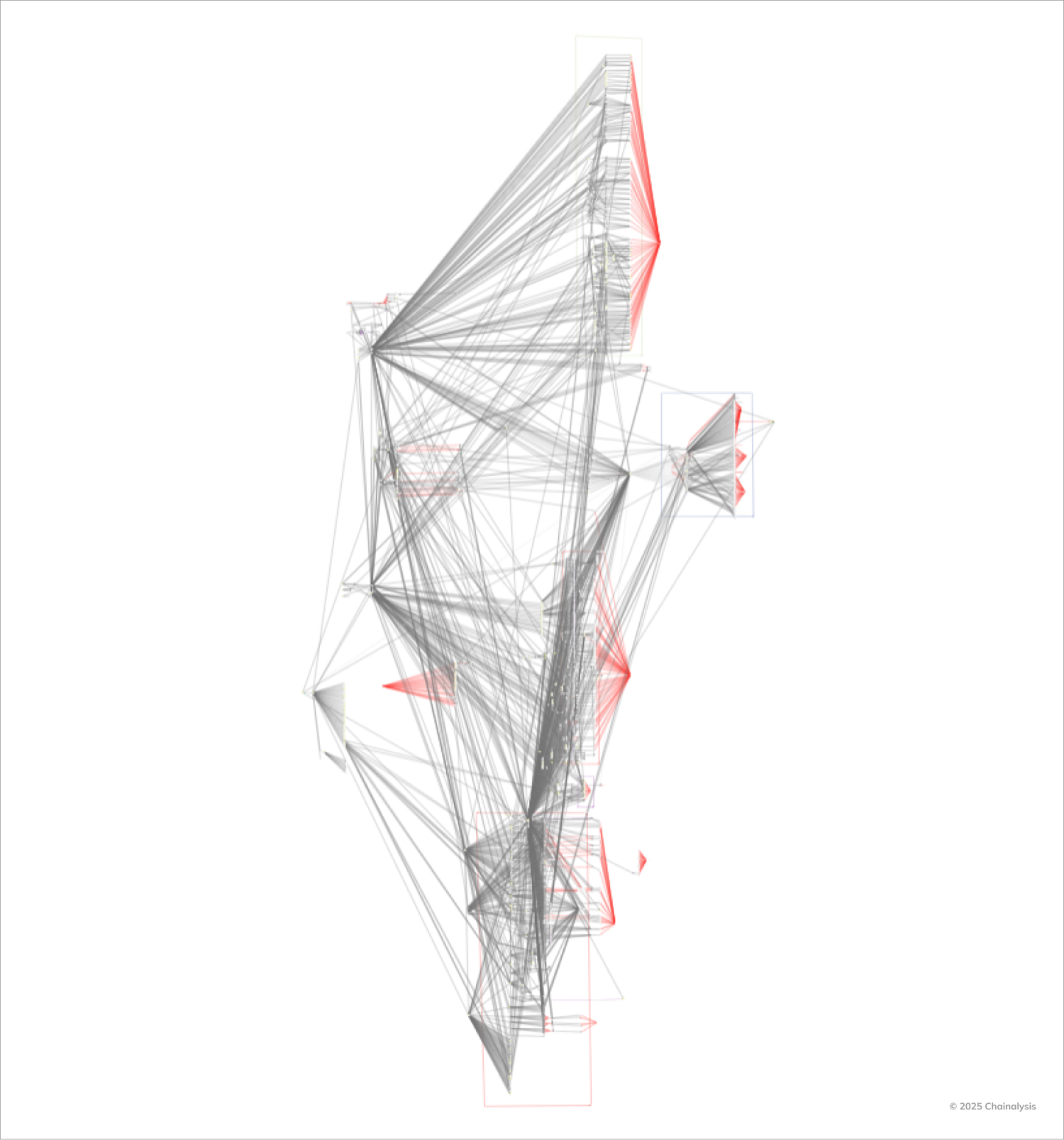
Collaboration of the industry following the hacking of Bybit
Despite the severity of the bybit’s attack, the inherent transparency of blockchain technology presents an important challenge for malicious actors who are trying to whiten stolen funds. Each transaction is recorded on a large public book, allowing the authorities and cybersecurity companies to trace and monitor illegal activities in real time.
Collaboration through the cryptographic ecosystem is essential in the fight against these threats. Bybit’s rapid response, including his insurance to Cover customer losses And his commitment to the Blockchain Medico-Legal Experts illustrates the commitment of the industry towards mutual support and resilience. By uniting resources and intelligence, the cryptographic community can strengthen its defenses against such sophisticated cyber attacks and work towards a more secure digital financial environment.
We work with our global teams, our customers and our partners in the public and private sectors to support several seizure and recovery paths in response to this attack. Already, we have worked with contacts in the industry to help freeze more than $ 40 million in bybit and continue to collaborate with public and private organizations to seize as much as possible. We will continue to provide updates on this subject.
This website contains links to third -party sites that are not under the control of Chainalysis, Inc. or its affiliates (collectively “Channel Analysis”). Access to this information does not imply the association, approval, approval or recommendation by chain analysis of the site or its operators, and the analysis chain is not responsible for the products, services or other contents hosted there.
This equipment is for information purposes only and is not intended to provide legal, tax, financial or investment advice. The recipients must consult their own advisers before making these types of decisions. The analysis chain has no responsibility for any decision taken or any other act or omission in relation to the use by the recipient of this material.
The analysis chain does not guarantee or justify the accuracy, completeness, speed, ability or validity of information in this report and will not be responsible for a complaint attributable to the errors, omissions or other inaccuracies of part of this material.


