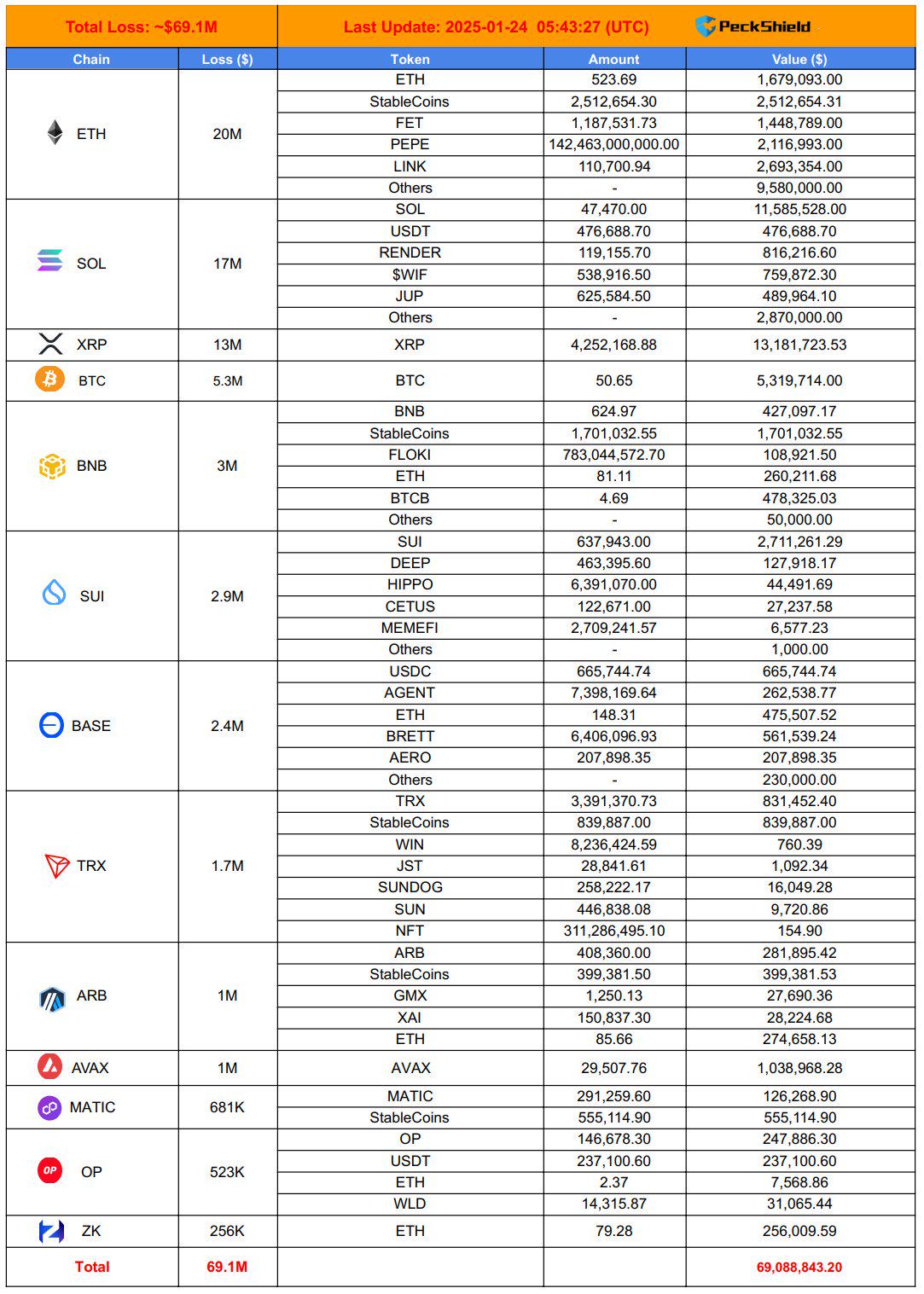
The losses of violations, hacks and scams in January 2025 were estimated at $ 98 million, with 28 cryptocurrency hacks, of which around 8 million dollars were allocated to phishing.
The strong safety points of zero hour technology have started! According to statistics from certain blockchain safety risk monitoring platforms, losses caused by vulnerabilities, pirates and fraud in January 2025 98 million US dollars, and 28 Cryptocurrency hacking attacks have occurred, of which about 8 million US dollars were allocated to phishing. However, compared to the loss of US $ 133 million in January 2024, it fell by 44.6% . Compared to the loss of 23.58 million US dollars in December 2024, it fell 56% .
Pirate attacks
7 typical security incidents
(1) On January 8, Orange Finance users (a DEFI protocol on Arbitrum) had more than $ 800,000. The attacker was able to access the administrative keys to the protocol and use these keys to carry out a malicious upgrade of the protocol contracts, thus stealing the portfolios of all users with valid token approvals for the protocol.
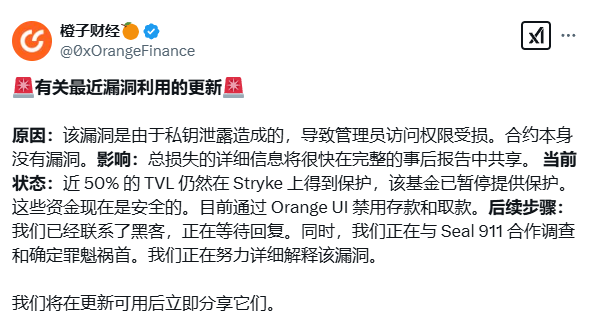
(2) On January 8, Moby had a private key leak which affected certain LP assets in certain protocols. They said it was not a security problem related to the smart protocol contract, but rather an attempted hacker to steal funds by simply improving existing intelligent contracts using private proxy keys stolen stolen proxies . Finally, Tonykebot took advantage of the lack of protection in the implementation of the Uups and carried out a successful white hat rescue, returning USDC 1.47 million which had been obtained by hackers who attacked the Protocol of Options of Moby channel to project owners.
(3) On January 13, according to the surveillance of the zero technology security team, UNLEnd on the EVM channel was attacked and lost around $ 197,000. The cause of this vulnerability was that when Unilend made a buy -back, it does not subtract the amount of warranty which should be transferred when calculating the amount of warranty, which leads to the amount of warranty after poor calculation being higher than the quantity warranty in fact belonging to the attacker, and the exchange that should not have succeeded was successfully completed. In the end, the attacker emptied the Steth tokens of the project.
For a detailed attack analysis, please click on this link:
Zero hour technology || Analysis of the Unlend attack
(4) On January 15, the team of the Zero Hour technology project detected several attacks against the Ethereum Sorra chain project, which caused a total loss of 41,000 USD. The cause of this vulnerability was that the Sorra project did not determine if the user had already withdrawn the reward when the user withdrew, which allowed the user to withdraw the reward several times operations. The attacker used the vulnerability above to initiate several transactions and remove all the sor tokens in the Sorra project.
For a detailed attack analysis, please click on this link:
Zero hour technology || Distress attack analysis
(5) On January 21, Forta detected a vulnerability of $ 324,000 on Theidolsnft.
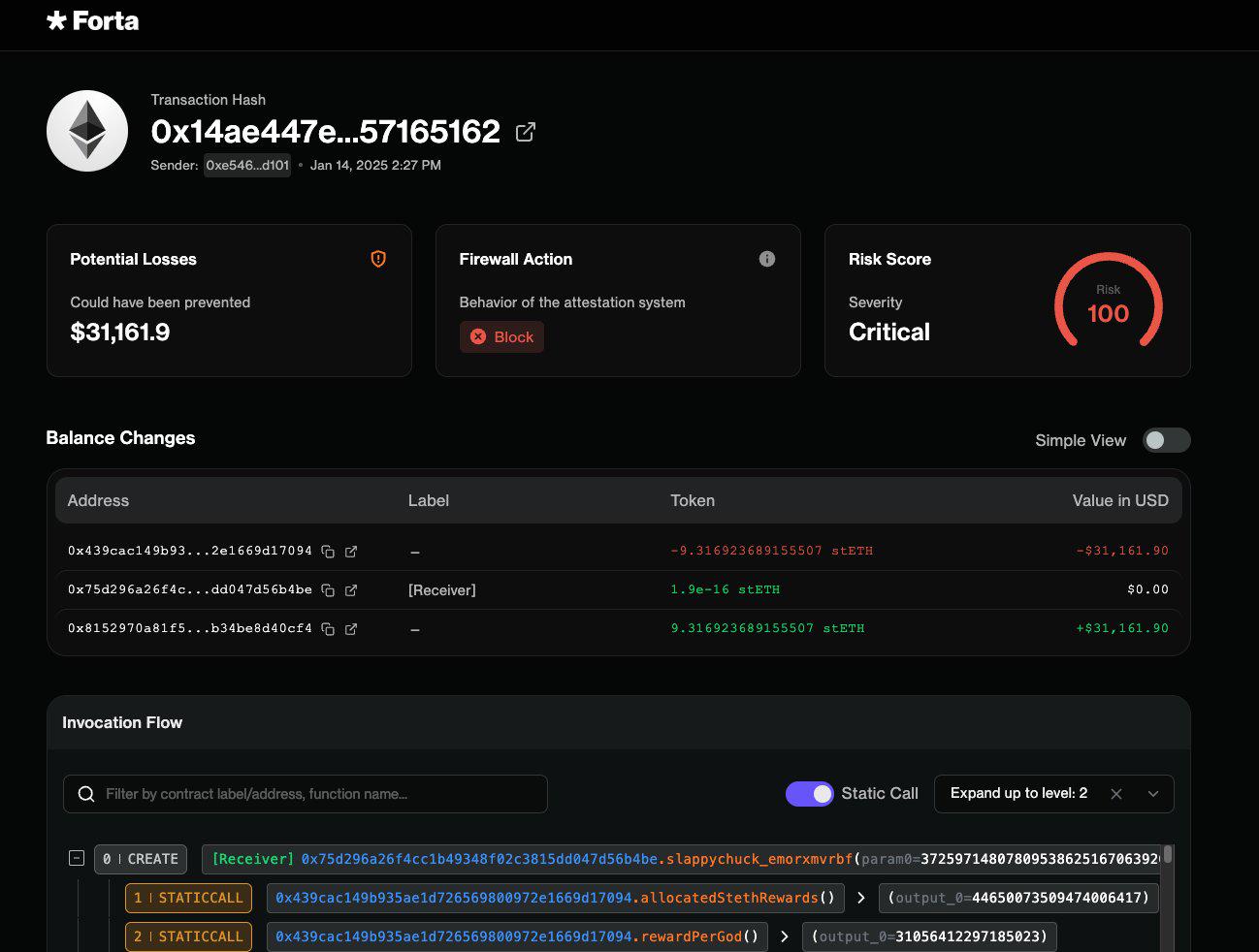
(6) On January 23, the hot portfolio of the Phemex cryptocurrency exchange based in Singapore was attacked, resulting in a loss of around $ 70 million.
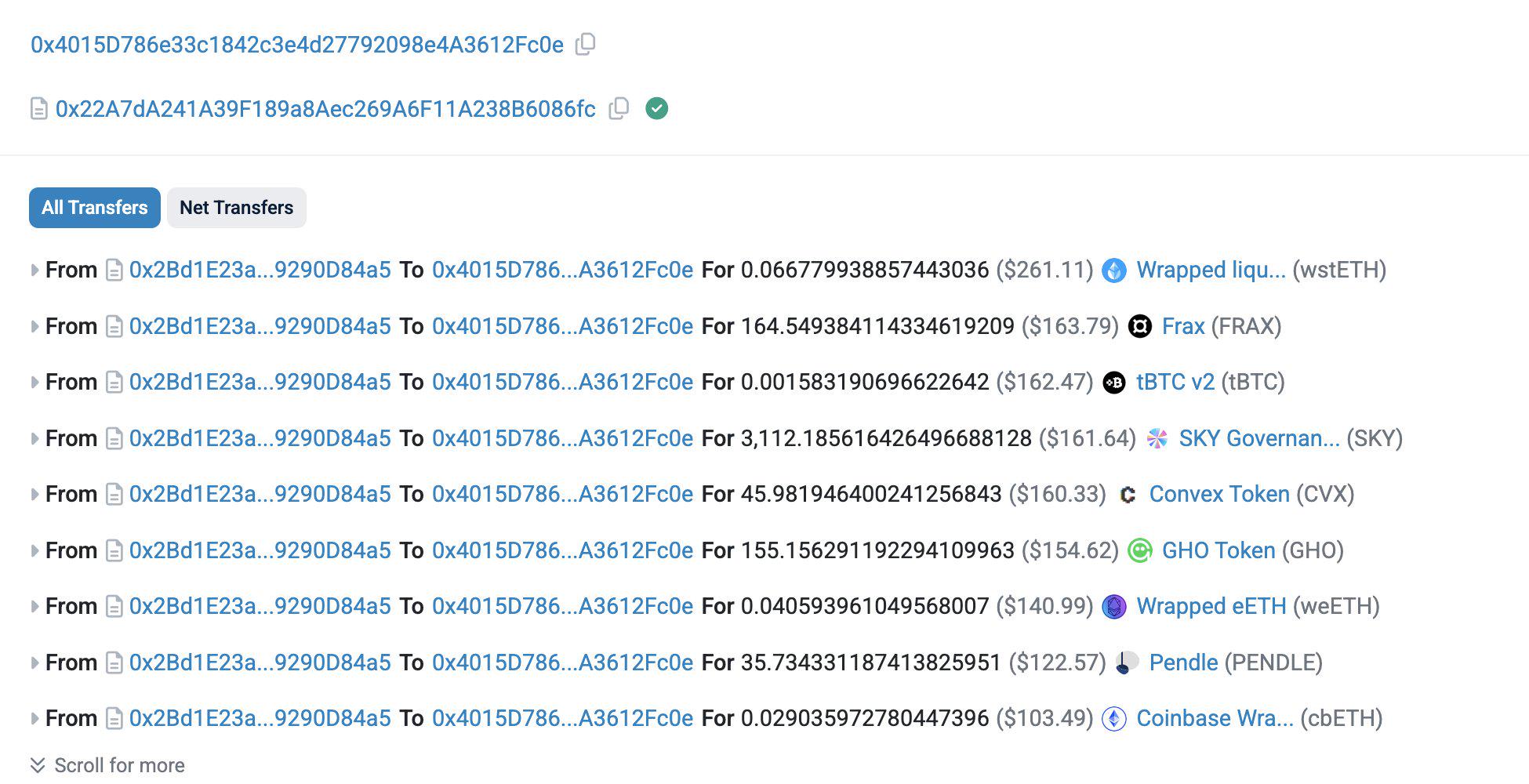
(7) On January 24, according to the surveillance of the Slowmist security team, due to the lack of validation of ODO entries, the vulnerability was used on several channels, resulting in a loss of around US $ 100,000. Odos tweeted that the attack has exploited a vulnerability in its audited executor contract and stole the revenues stored in the contract, but did not affect any user funds.
Shooting / phishing scam
10 typical safety incidents
(1) On January 2, a virtual holder $ holding approximately 39 times ($ 196,396) of tokens lost all his tokens due to a phishing transaction “increase limit”.
(2) On January 3, an $ RLB holder lost all his tokens worth around $ 1 million due to a “united” phishing “signature.
(3) On January 6, the address from 0x5167 lost $ 155,256 in properly after having signed a phishing transaction to “increase the allowance”.
(4) On January 7, the address starting with 0x8536 Lost Tokens worth $ 103,020 after signing the phishing transaction “Uniswap allow2”.
(5) On January 8, the address starting with 0x3402 lost $ Olas, $ sekoia, $ virtual and $ fjo worth $ 474,422 after signing several phishing signatures.
(6) On January 14, the address starting with 0x00C0 lost $ virtual worth $ 263,255 after signing a phishing transaction.
(7) On January 17, the address starting with 0x80DC lost usualusdc + worth $ 426,106 after signing a “license” signature.
(8) On January 20, the address starting with 0x1e70 lost $ 135,068 after signing the Signature of Phishing “Authoriser”.
(9) On January 22, the address from 0x3149 lost $ 553,045 $ Paxg after signing a “transfer” phishing transaction.
(10) On January 29, the address from 0xeb2 lost $ $ 384,645 after signing the phishing transaction “Increase”.
To summarize
Cryptocurrency phishing scams stole $ 10.25 million from $ 9,220 in January, a decrease of 56% compared to the $ 23.58 million in losses in December. However, criminals evolve and use more sophisticated methods of attack.
The Zero Time technology security team recommends that project owners are still vigilant and reminds users to be wary of phishing attacks. Users are advised to fully understand the history and the project team before participating in the project and carefully choosing investment projects. In addition, training in internal security and the management of the authorities should be carried out, and professional security companies must be carried out to carry out audits and conduct investigations on the a history of the project before the project is online.
Author: 零时科技
This article reflects the opinions of the Panews columnist and does not represent the position of panews. Panews does not assume legal responsibility. The article and opinions do not constitute investment advice.
Image source : 零时科技 If there is a counterfeit, please contact the author to delete it.


