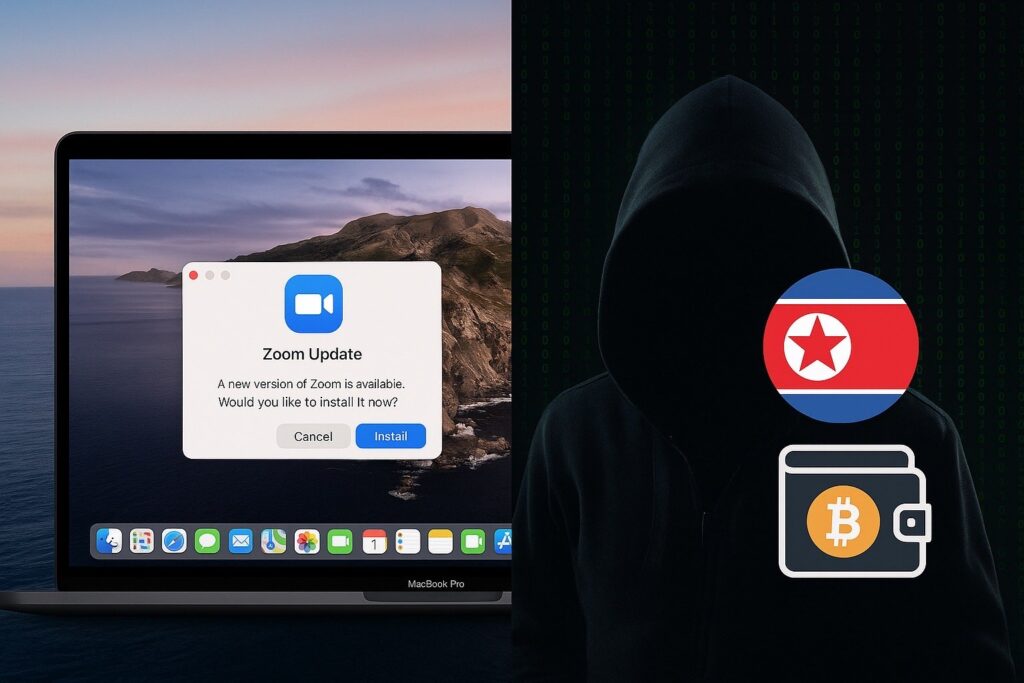
A newly discovered malware strain called Nimdoor raises alarms through the cryptographic community – in particular for macOS users.
The researchers retraced malicious software to the north-Korean hacking groups supported by the state, which now target cryptocurrency holders with surprisingly sophisticated campaign.
Attackers use social engineering To send false zoom updates via platforms like Telegram and Google Meet, encouraging users to install what seems to be an update of videoconferencing – but is actually a custom -stolen door.
Written in the Obscur Nim Programming Language, Nimdoor is difficult for antivirus tools to detect.
Once installed, it quietly exfiltrates sensitive data such as passwords stored by the browser, telegram session data and Crypto portfolio identification.
He even monitors the contents of the clipboard, looking for seed sentences or wallet addresses.
Malware is resettled whenever it is arrested, which makes it particularly difficult to remove once integrated.
Crypto portfolios are the main target
The rise in malware like Nimdoor reflects an increasing trend: cybercriminals no longer hunt passwords – they go directly for cryptographic wallets.
Nimdoor is designed to target browser -based wallets, storage of unsecured keys and users who copy and stick sensitive information such as private keys or seed phrases.
If you are counting on a browser extension or an exchange portfolio, you are mainly at risk. These platforms store data in predictable places – which is exactly what this type of malware is designed to operate.
Although MacOS has historically been considered a safer operating system, Nimdoor proves that no system is immune when the attackers are also determined.
How to protect your crypto in 2025
As these threats evolve, the best defense remains the same: self -assurance combined with strong operational habits – also known as the portfolio hygiene.
Portfolio hygiene refers to daily habits that protect your keys, such as how you store seed sentences, copy addresses and use secure wallets.
Here are some best practices to reduce your risks:
- Avoid browser portfolios that store keys in local storage or are accessible via your browser profile.
- Use hardware portfolios or mobile self-cooker wallets with secure enclaves and biometric access.
- Never store your seed phrase on your computer, clipboard, screenshots or cloud storage.
- Update your bone and antivirus software regularly – and never install the zoom updates from unofficial cat links or messages.
Staying safe in 2025 means understanding that threats are evolving – and that portfolio hygiene, storage practices and updating sources of all materials.
The cryptocurrency remains a powerful form of control, but only when it is managed with care and awareness of risks.
Don’t wait for alarm clock
Nimdoor is only the last example of the speed with which the landscape of the threat evolves – and how crypto holders become privileged targets. It is not only a single part of malicious software. This is a fundamental change in the operation of pirates: stealth code, more credible traps and an implacable accent on digital assets.
Staying safe does not mean being paranoid – it means being prepared. Understanding the functioning of these threats is the first step.
How to secure your crypto tokens
Whether you hold a little or a lot, using secure and self -careful solutions is not just part of the game – it is the game in which each other is built.
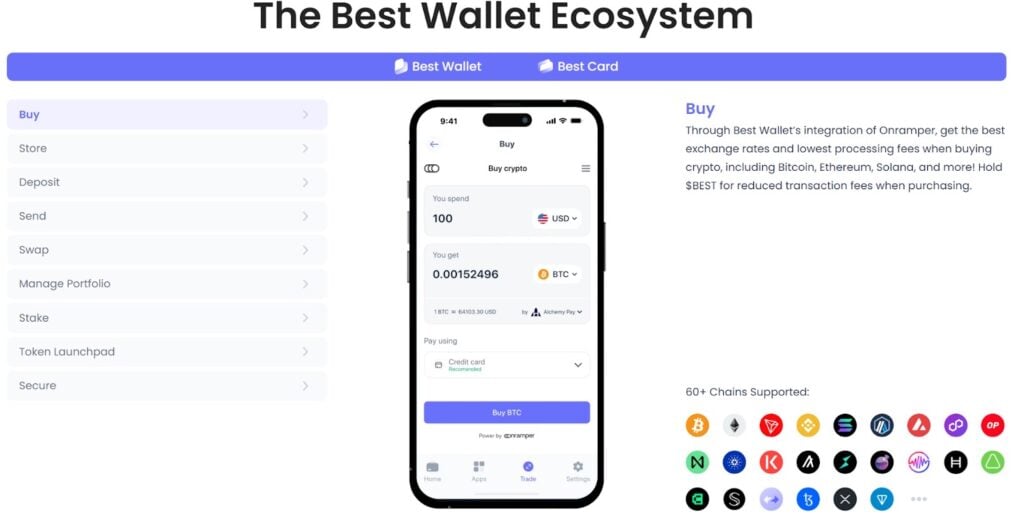
Among the best options to fully secure your Crypto tokens Figure Best walletA complete NO-KYC solution which gives users a total control over their assets, which makes it immune to the increase in targeted portfolio scams.
More importantly, its security focused design, powered by the integration of fire blocks, guarantees that there is no unique failure point that cybercriminals can exploit.
Other key safety measures such as unique passing codes, biometric authentication and two factors, regular security updates and communication via its social networks, and many others, help protect users from phishing attacks, malware and drainage software that continue to spread in cryptographic space.
But security is only one of the key elements that have solidified the position of the best portfolio for the best wallet. The best portfolio also stands out by offering advanced trading features, beyond the basic portfolio capacities such as storage, crossing and payment of the Fiat.
Some of the high features of the best portfolio application include an aggregator of clearing, a pavingst of tokens, transactions without gas token, MEV protection, igaming, derivative trading, wallet monitoring and much more, making a one -stop shop for any crypto.
And as the market ripens and security risks become more difficult to ignore, experts think that self-conservative tools like the best portfolio have become more critical than ever.
This article was provided by one of our business partners and does not reflect the opinion of Cryptonomist. Please note that our business partners can use affiliation programs to generate income via the links in this article.